If you're engaged in any form of intensive data processing or software development, chances are you've encountered SSH (Secure Shell). This powerful tool is ubiquitous in the IT industry for its versatility, security, and ease of use. This article will guide you through the basics of SSH usage, provide examples, and explore the advanced feature of tunneling to use remote networks. We'll also touch on how to configure web navigation using the remote computer's location, setting it up using popular web browsers such as Firefox and Chrome.
Understanding SSH
SSH is an encrypted protocol used to connect and authenticate to remote servers. With SSH, you can run commands on a remote server. SSH operates on TCP port 22 by default, but this can be changed if required.
Typically, I use this tool to establish a connection with a server, often maintained by a corporation or academic institution, to execute complex analyses that demand substantial computational resources and extended processing time.
Using SSH for Remote Access
To access a remote Linux machine from your local computer, you simply open a terminal and type:
ssh username@remote_host
username is the account you want to access, and remote_host is the IP address or domain name of the remote machine. Once connected, you can execute commands as if you were physically present on the machine.
Please be aware that your remote server must be pre-configured to permit SSH access. For the purpose of this guide, we are assuming that this setup is already in place. If you're tasked with configuring it yourself, you'll likely find this other article helpful, it shows how to Configure OpenSSH on Ubuntu Server.
SSH Tunneling: A Powerful Feature
One of the lesser-known but very powerful features of SSH is tunneling. SSH tunneling allows you to forward your local internet traffic to a remote machine via the SSH connection. This creates a secure conduit between your machine and the remote server, effectively allowing you to browse the web as if you were located at the remote machine
This can be useful for many purposes, such as accessing a website from the IP of the remote machine or bypassing geo-blocked content.
To create an SSH tunnel, you can use the -D flag followed by a port number:
ssh -ND 8080 username@remote_host
This command establishes a SOCKS proxy that channels all your local machine's internet traffic through the remote machine, using the SSH connection as a conduit. While the -N flag is optional, its inclusion ensures that SSH does not execute any commands on the remote server, instead solely opening the connection for forwarding purposes.
The prompt may appear to be "frozen", but rest assured, it's operating as intended. If you want to cancel the operation: ctrl + c
Using SSH Tunnels with Firefox and Chrome
After setting up your SSH tunnel, you can configure your web browser to use this tunnel. Here's how to do it with Firefox and Chrome:
Firefox
To begin, launch Firefox and navigate to the Preferences page. You can do this by entering
about:preferencesin the URL bar.Use the search form to look for "sock" and click the button "Settings..."
In the Connection Settings window, select the "Manual proxy configuration" radio button.
Enter "127.0.0.1" in the SOCKS Host field and "8080" (or whatever port you chose) in the Port field.
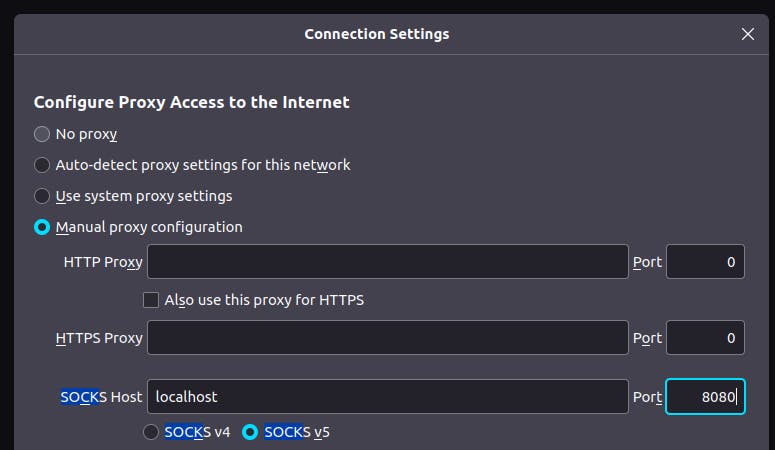
Ensure the "SOCKS v5" checkbox is checked and click "OK".
Now you'll be browsing in Firefox using the remote internet connection. You can check it by consulting the ip you're using on sites like whatismyip.com.
Remember to set it back to "No proxy" when you want to use your own internet connection again.
Chrome
Unfortunately, Chrome lacks built-in support for SOCKS proxies. Nevertheless, you can utilize an extension, such as Socks5 Configurator, to enable this functionality. The configuration process is quite straightforward, so we won't duplicate the content here. If you encounter any difficulties, feel free to leave a comment, and we'll be happy to help.
Conclusion
You can use SSH to do your common server stuff, like executing commands and submitting data-intensive processes, and you can also use SSH to use a remote internet connection. The setup process for Firefox and Chrome is simple. As with any powerful tool, ensure you're using SSH responsibly and ethically.
Just a reminder: refrain from using your server for activities that could raise eyebrows. The IP address of your company (or university) can easily be linked back to you. If anonymous browsing is your primary goal, consider opting for a VPN provider instead. This ensures a higher degree of privacy and limits potential repercussions.

